How to create application rules of the firewall on windows profile
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
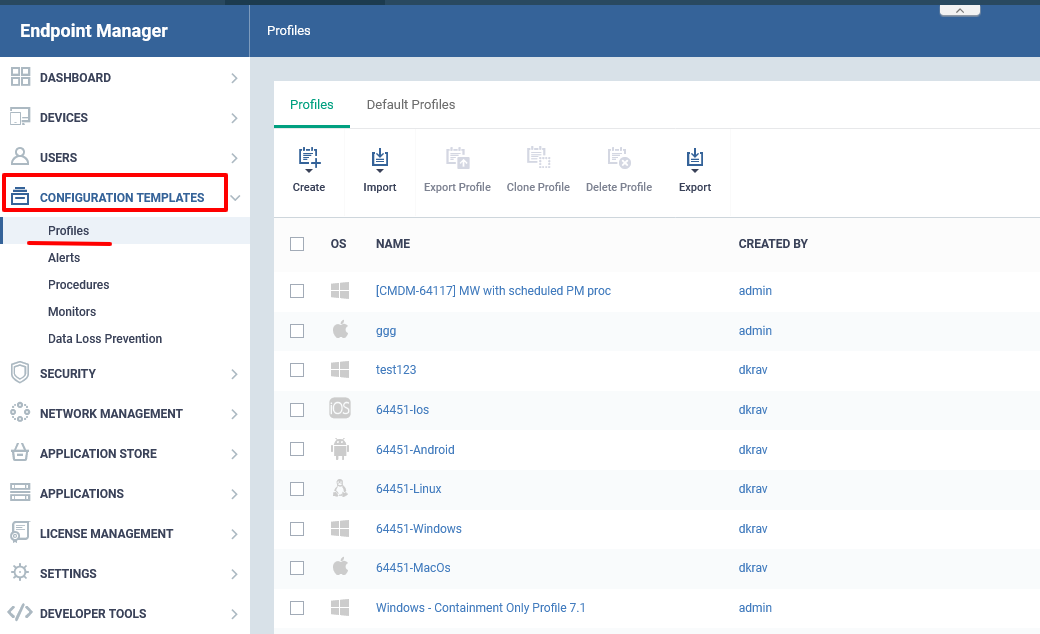
Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles
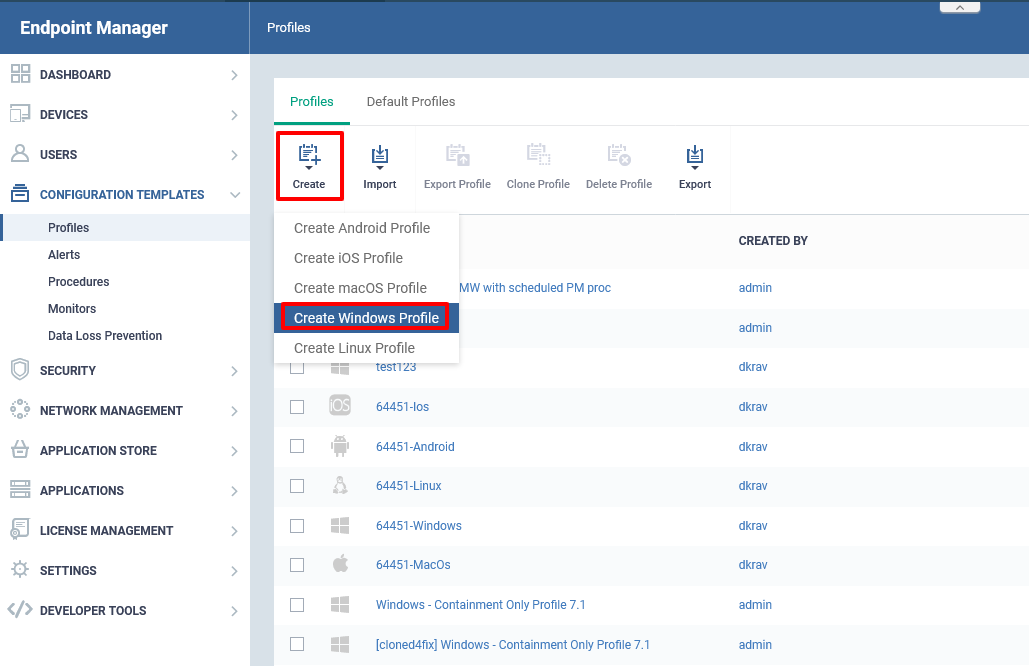
Step [2]: Click Create icon and Choose the Create Windows Profile from the drop down menu
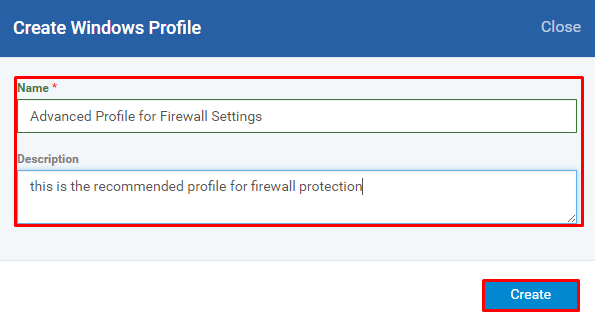
Step [3]: Enter the Name, Description of the profile and Click the Create button
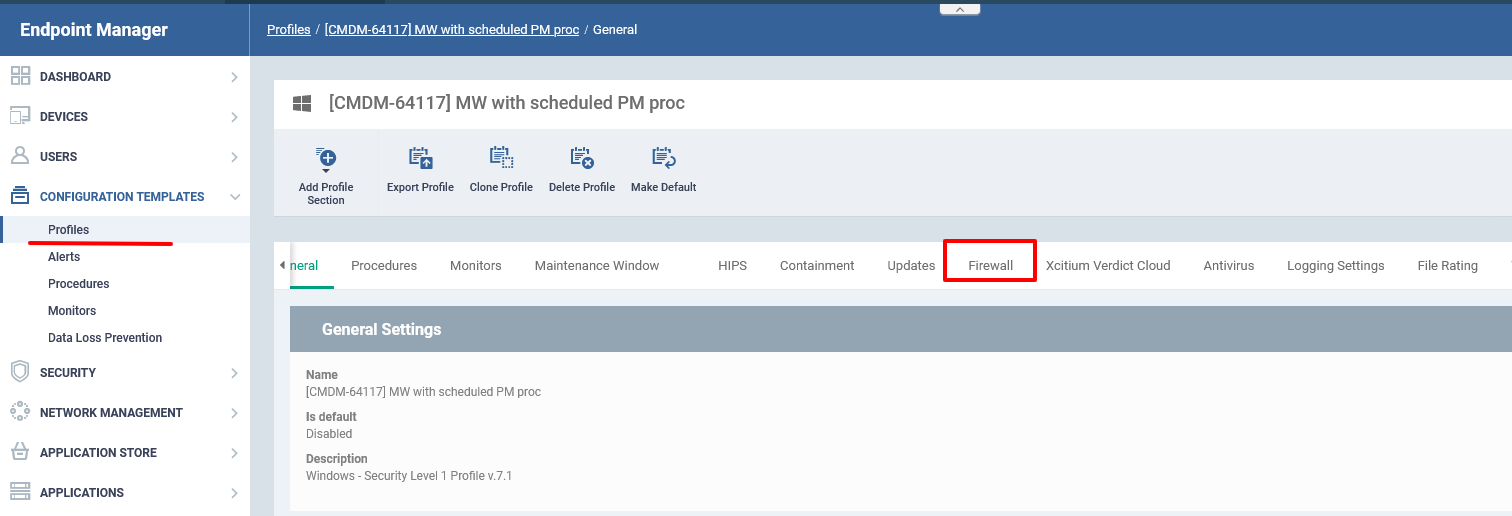
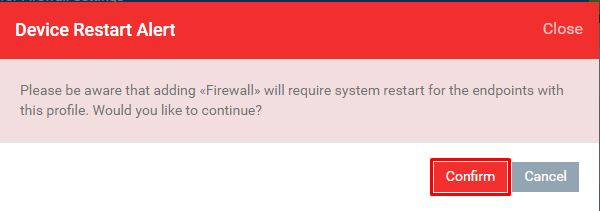
Step [4]: Click Add Profile Section and Choose Firewall from the drop down
Step [5]: Click the Confirm button
Note:
There are some necessary settings to be completed to continue further on advanced firewall profile such as
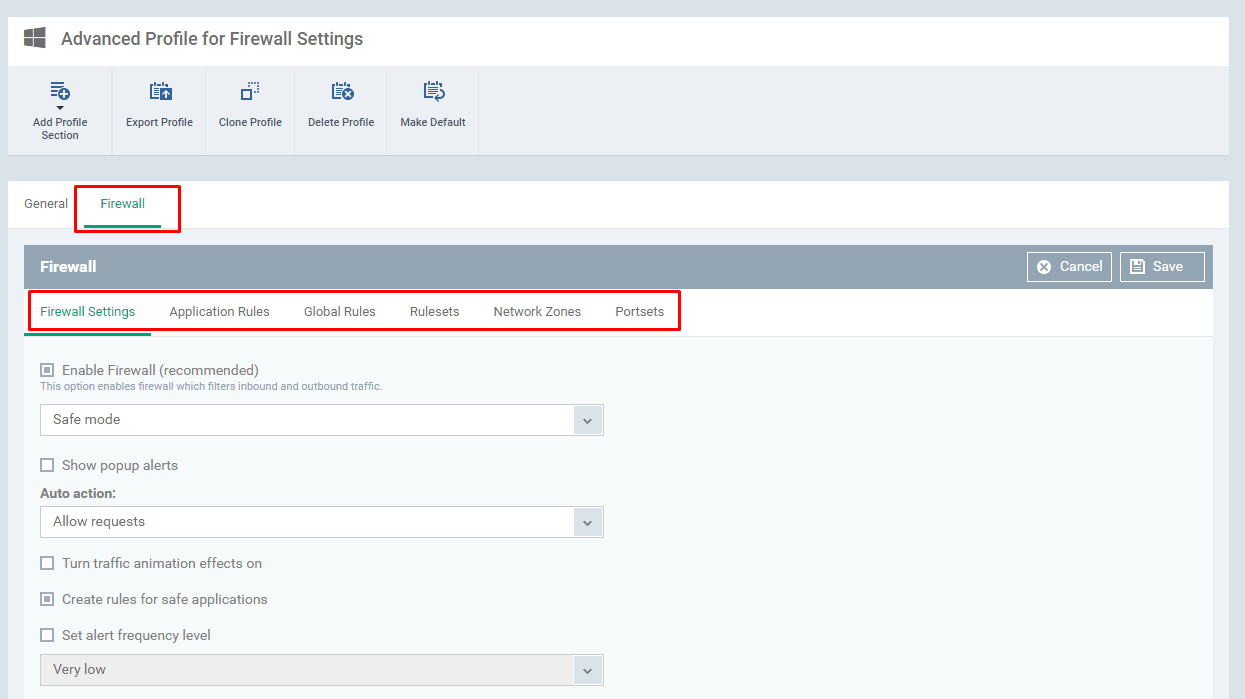
Step [6]: Select the tab Application Rules
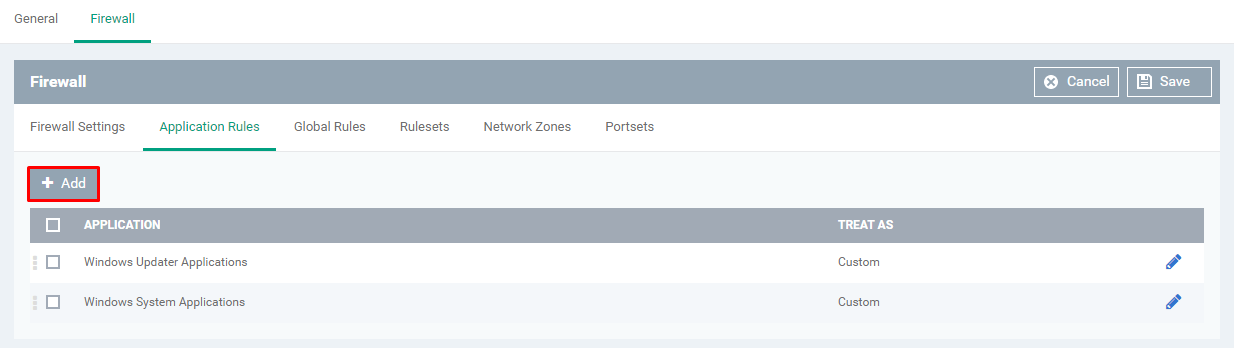
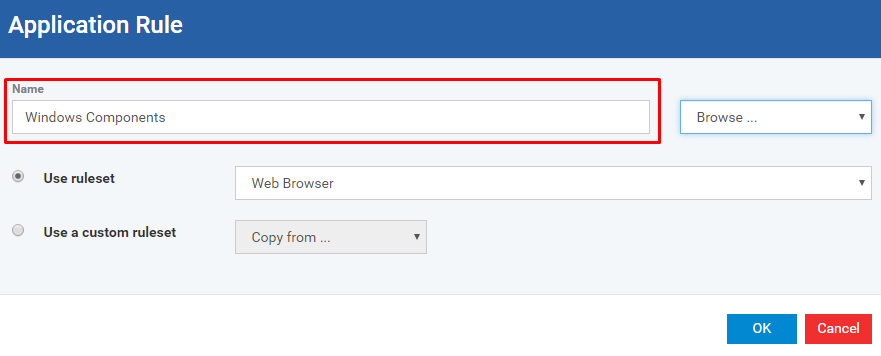
Step [7]: Click Add button and Fill the form Application Rule, if you want to add more application rules, Otherwise leave the setting as in the beginning.
Step [8]: Choose the choice 'using existing target' or 'using new target'
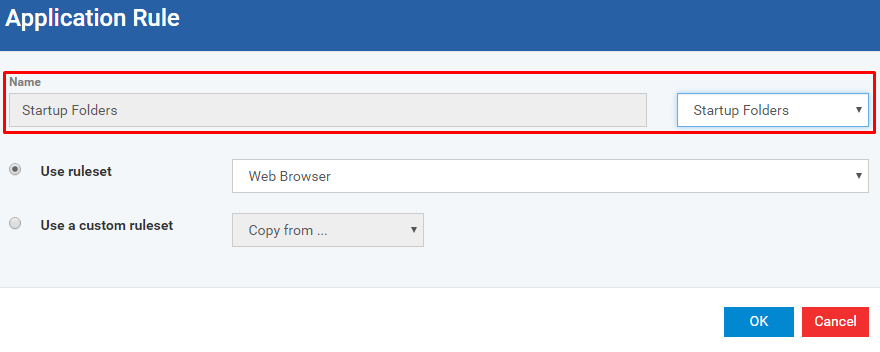
Enter the name if you would like to create a new file group target.
Choose the choice 'using existing target' or 'using new target'
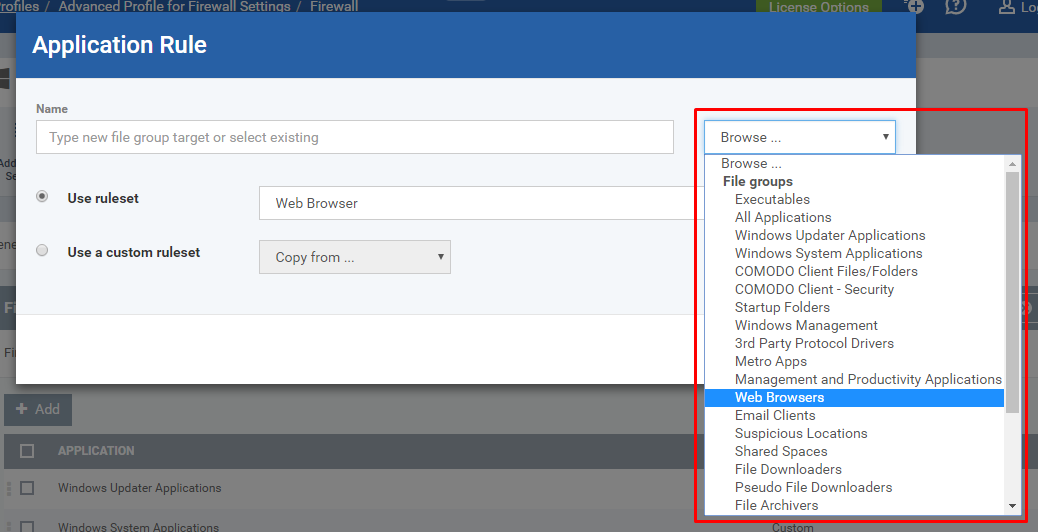
If you would like to use existing target then Click the drop down Browser and Choose the specific option from there
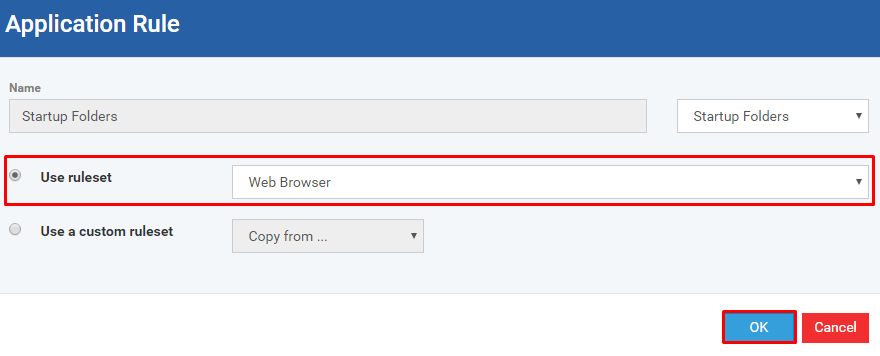
Step [9]: There are two possible options to continue further with adding new ruleset, Choose the option 'Use ruleset' or 'Use a custom ruleset' from the form
- Use ruleset - predefined ruleset by Xcitium
- Use a custom ruleset - custom ruleset which can be set by the user (you)
If you would like to create a predefined ruleset,
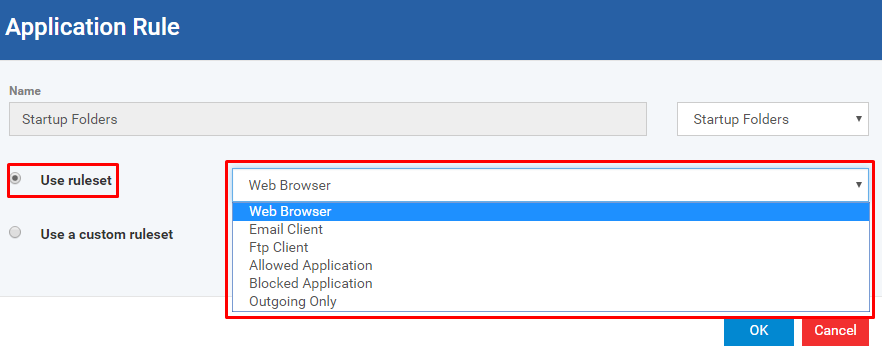
Click the radio button 'Use ruleset'
Options:
- Web Browser - all applications belongs to browse the internet, Example: IE, Firefox, Chrome, Opera, and etc.
- Email Client - all applications belongs to email client interface, Example: Thunderbird, and etc.
- FTP Client - all applications belongs to FTP interface, Example: FileZilla, and so on
- Allowed Application - all applications which are set to be allowed
- Blocked Application - all applications which are set to be blocked
- Outgoing Only - all applications which are set to be allowed for outgoing connection
Choose application category from the drop down and click OK button
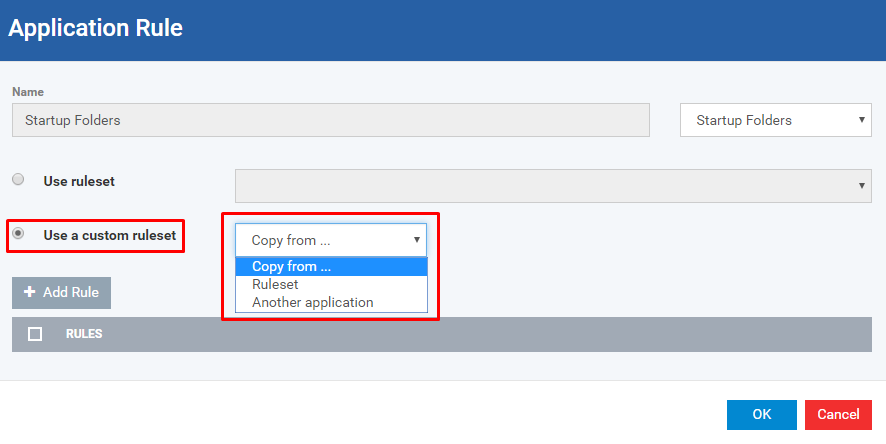
If you would like to copy from the existing rulesets,
Click the radio button 'Use a custom ruleset' and Click 'Copy from...' drop down
Options:
- Ruleset - Which helps to copy from desired existing predefined rulesets
- Another Application - Which helps to copy from desired existing user-defined rulesets
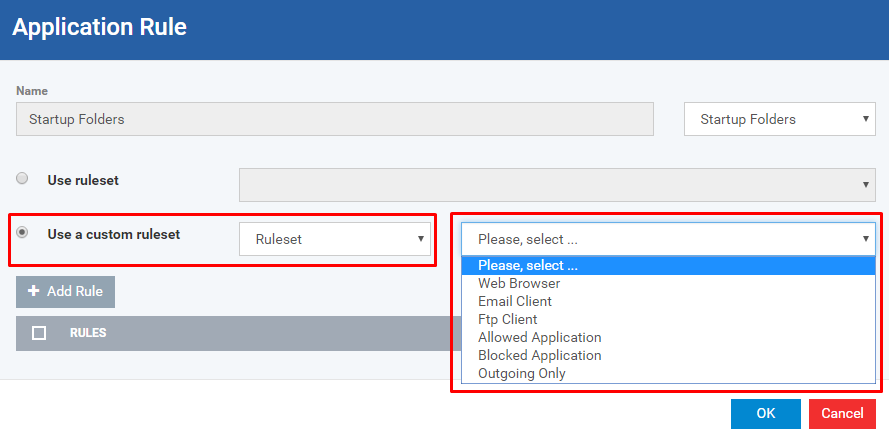
If you want to use predefined Ruleset then Choose Ruleset from the 'Copy from...' dropdown
Choose desired predefined ruleset from the drop down. Example: Web Browser
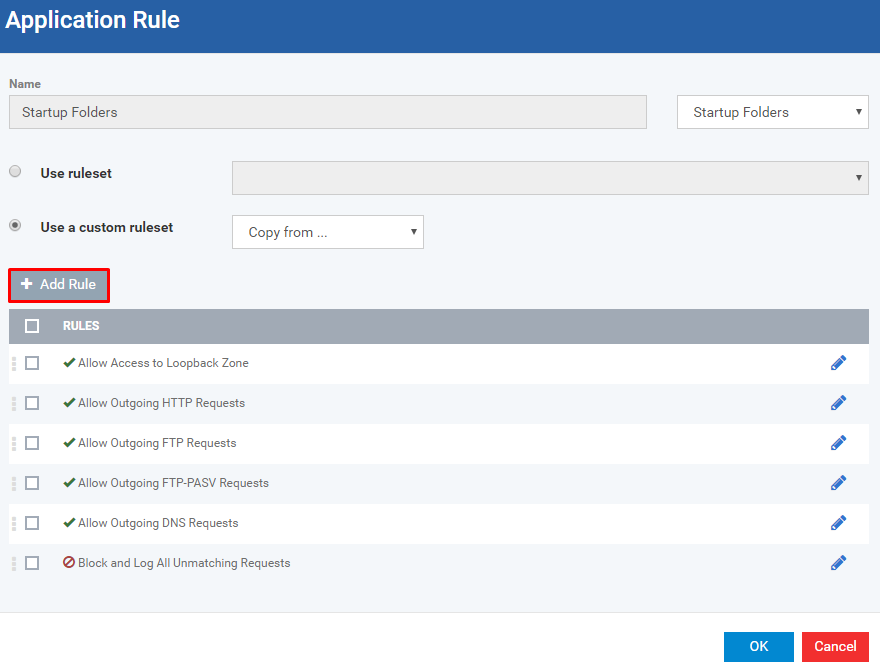
Explanation:
From the table, you can add or remove rules or you can modify a specific rule from the table
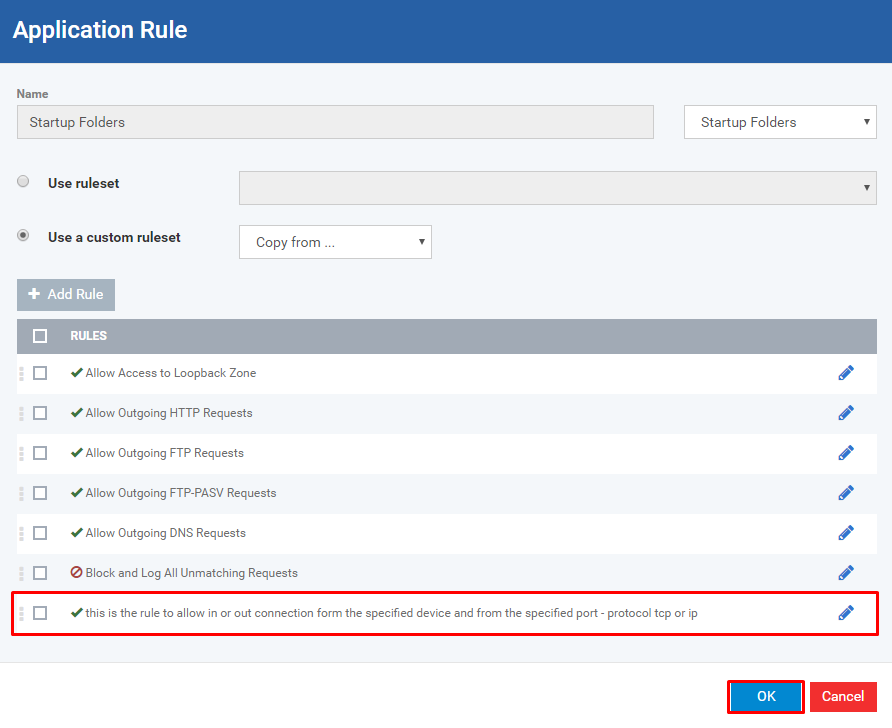
If you want to add rules then click Add Rule button
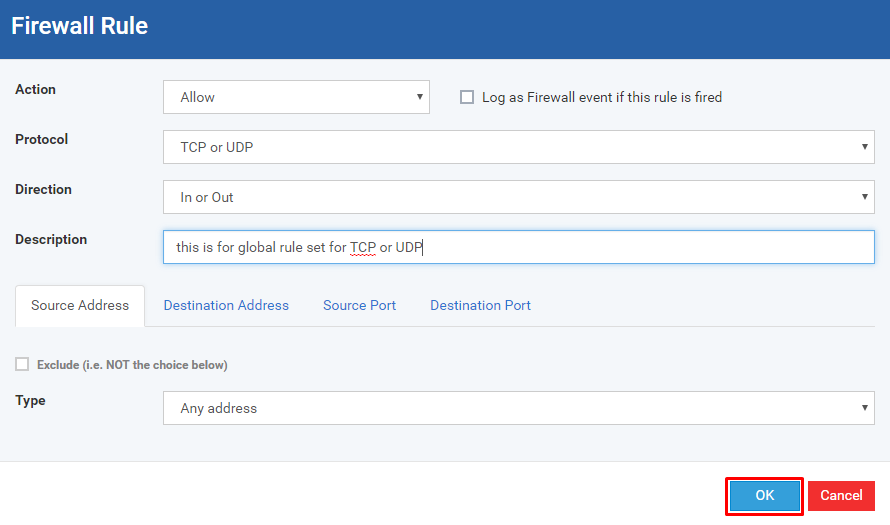
Fill the Firewall Rule form and Click OK button to submit
Explanation:
Action - Allows setting the action that firewall would take over the rule
-
- Allow - If chosen, which allows the connection
- Block - If chosen, which blocks the connection
- Ask - If chosen, which asks you (user) to confirm the connection to be allowed or blocked
Log as Firewall event if this rule is fired - Can be enabled or disabled for logging the event into Firewall Events when it is triggered
Protocol - Allows setting the type of protocol for the rule
-
- TCP - If chosen, the rule applied only for TCP connection
- UDP - If chosen, the rule applied only for UDP connection
- TCP or UDP - If chosen, the rule applied only for TCP or UDP connection
- ICMP - If chosen, the rule applied only to ICMP connection
- IP - If chosen, the rule applied only for IP connection
Direction - Allows setting the direction of the connection
-
- In - Incoming connection
- Out - Outgoing connection
- In or Out - Either Incoming or Outgoing connection
Description - Allows describing the rule
Source Address - Allows you to apply the rule for the Address of the device that tries to access your endpoint
Destination Address - Allows you to apply the rule for the Address of the device that your endpoint tries to access it
Options:
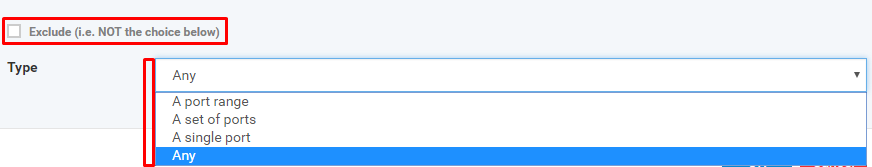
Exclude - If enabled, allows to set up devices to be excluded from the rule
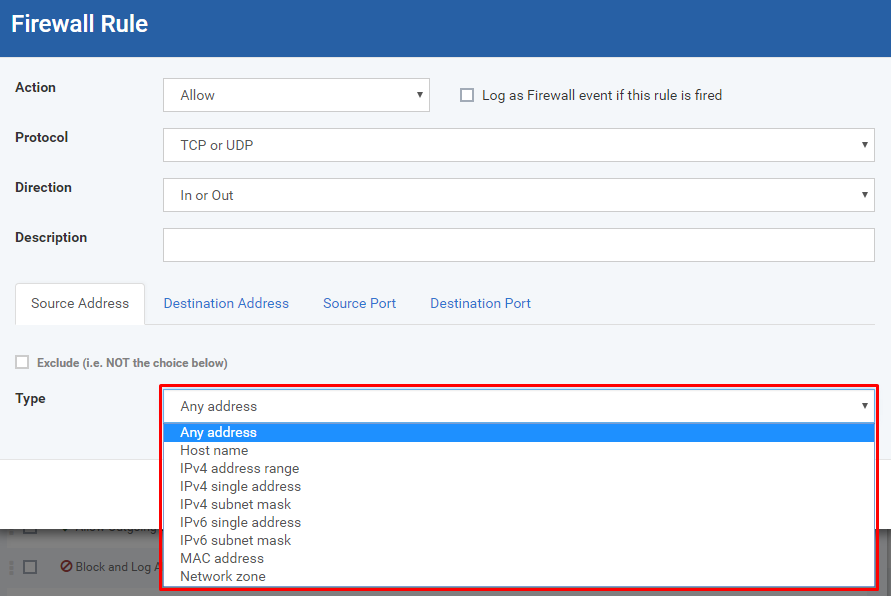
Type - Types of the Address of the device
Any address - any devices
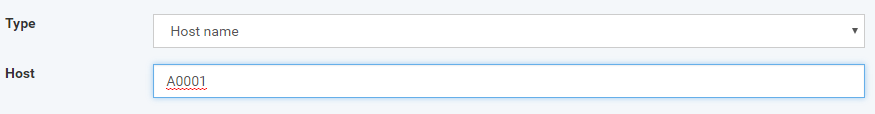
Hostname - device that has the same name of hostname
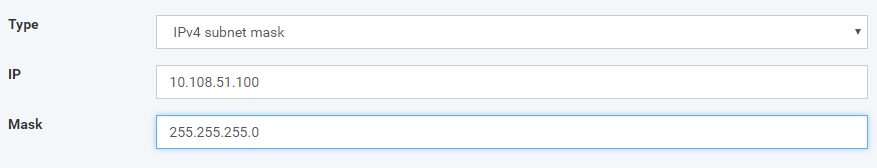
IPv4 address range - device from the range of IP addresses
IPv4 single address - device from the same IP address
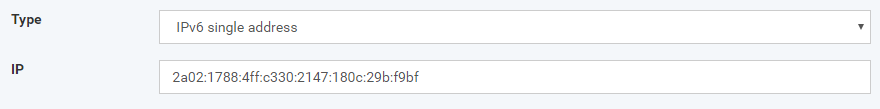
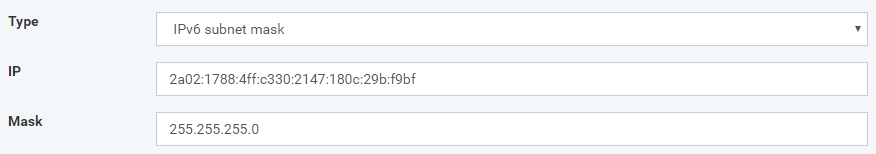
IPv6 single address - device from the same IP address
IPv6 single address - device from the same IP address
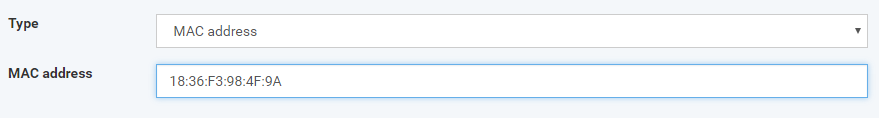
MAC address - device that has the same MAC address
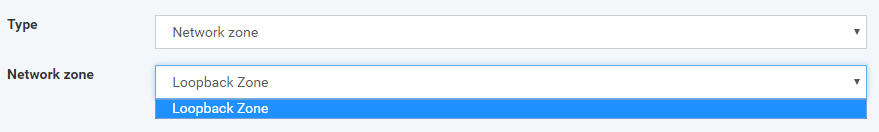
Network zone - device that belongs the same network zone
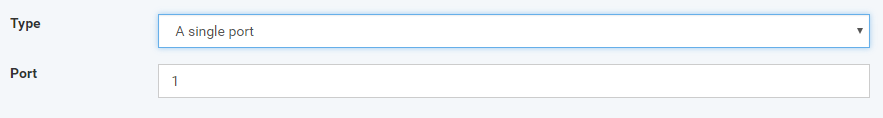
Source Port - Allows you to apply the rule for the port number or ranges of the device that tries to access your endpoint
Destination Port - Allows you to apply the rule for the port number or ranges of the device that your endpoint tries to access it
Options:
Exclude - If enabled, allows to set up the port number or range to be excluded from the rule
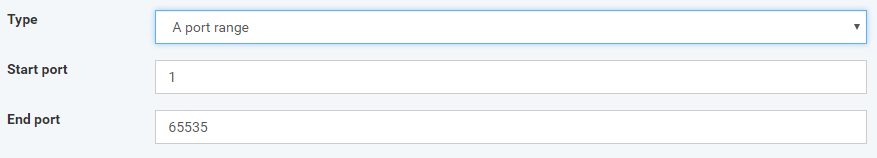
A port range - port from the range of ports
A set of ports - port from the set of ports
A single port - port which is same of the given port
Any - any port
Check whether you have the specified rule and Click OK button
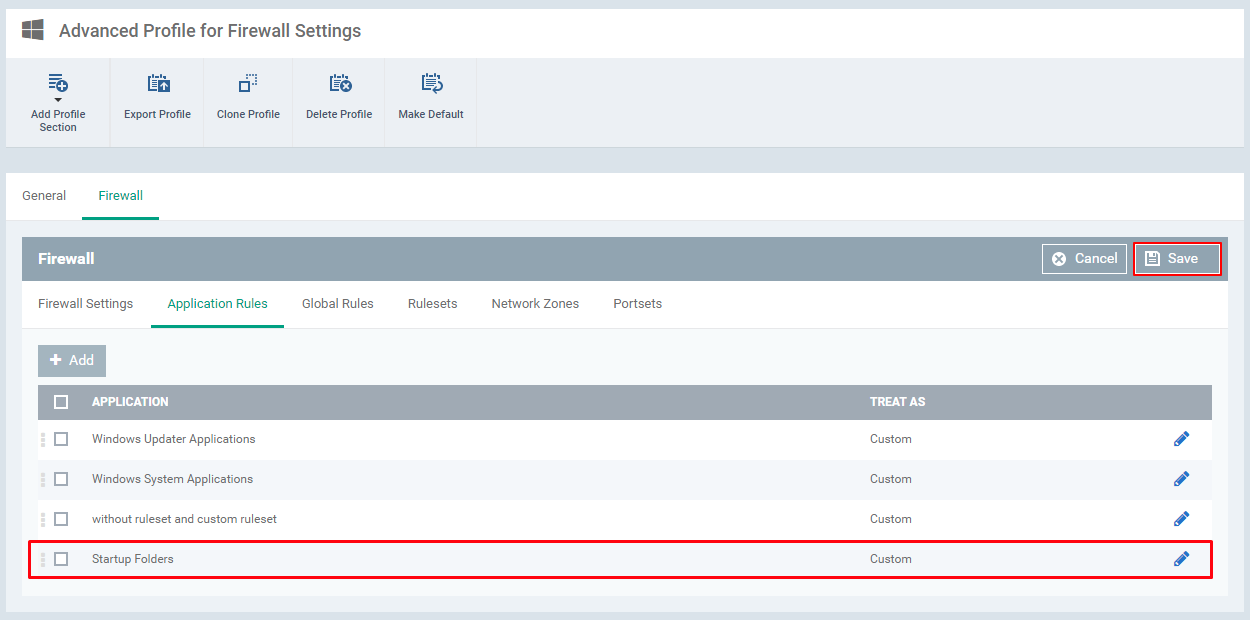
Step [10]: Check whether you have the application rule on Application Rules and Click Save button
Step [11]: Click Profiles menu and check whether the profile has been added to the table.