How to identify vulnerable devices and install security patches
Open Endpoint Manager > Click ‘Applications' > 'Vulnerability Management’
- The vulnerability management interface lets you view known weaknesses found on your devices, along with their CVE (common vulnerabilities and exposures) rating.
- You can view which devices are affected and install patches as required.
Use the links below to jump to the task you need help with:
- Open the vulnerability management area
- View vulnerability details
- Patch selected vulnerabilities
- Install patches on selected devices
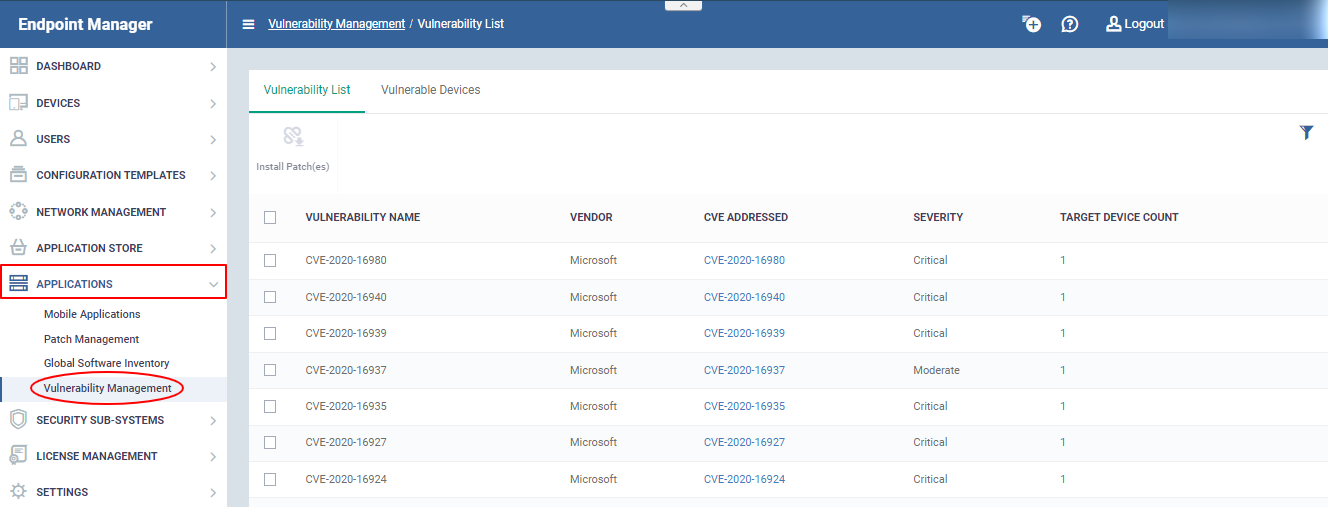
Open the vulnerability management area
- Open Endpoint Manager
- Click 'Applications' > 'Vulnerability Management'
The interface has two tabs, each of which offers a different view of the vulnerabilities:
- Vulnerability List – Shows discovered vulnerabilities and the number of devices affected by each.
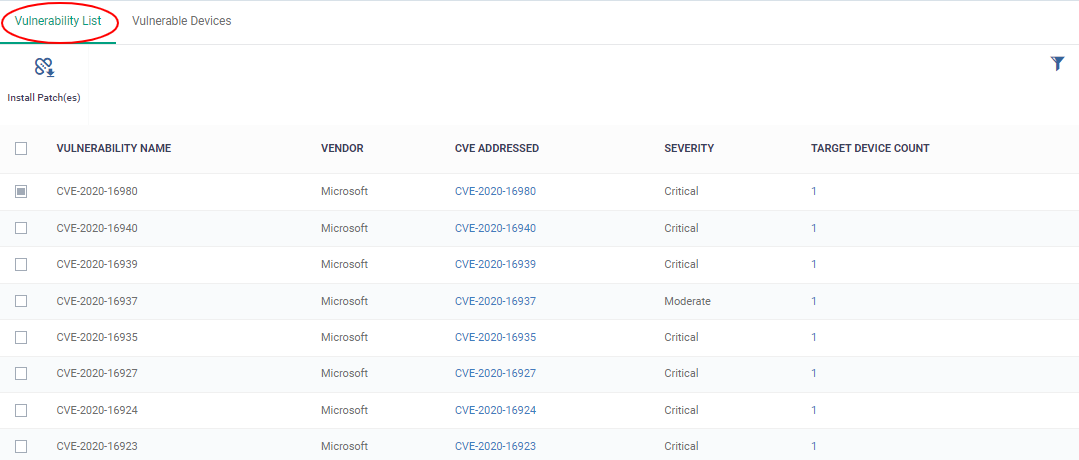
Apply corrective patches:
- Click the number in the 'Target Device Count' column
- Select the devices you want to patch
- Click the 'Install Patch' button above the table
- Click the number in the 'Target Device Count' column
- Vulnerable Devices – Shows devices affected by vulnerabilities. Lets you patch all vulnerabilities on a device with a single click.
- Click 'Applications' > 'Vulnerability Management'
- Click the 'Vulnerability List' tab
- The vulnerability list can be sorted in ascending or descending by the column under the Vulnerability Management.
- Click 'Install Patches' the vulnerabilities will be applied to the targeted devices.
- Vulnerability Name - The vulnerability identifier. This is the same as the CVE code.
- Vendor - Developer of the affected software and the corresponding patch
- CVE Addressed - Click to view vulnerability details, vendor and affected devices. See View details of a vulnerability threat to read more.
- Severity - Criticality of the vulnerability. The possible levels are:
- Critical - Vulnerabilities that can be exploited without warnings or prompts. Examples include remote elevation of privileges exploits that allow attackers to write to the file system, or execute arbitrary code without user interaction. You should patch critical vulnerabilities as soon as possible.
- Important - A vulnerability that could compromise the confidentiality, integrity, or availability of user data if exploited. The distinguishing factor between critical and important is that important vulnerabilities show some warning or prompt to the user. For example, local escalation of privilege exploits, or the execution of arbitrary code which requires extensive user action. Again, you should patch important vulnerabilities as soon as possible.
- Moderate - The likelihood of exploitation is largely mitigated by factors such as default configuration, auditing, or difficulty of exploitation. Moderate vulnerabilities usually require specific scenarios, locations or other prerequisites. We recommend you consider patching moderate vulnerabilities.
- Low - A vulnerability whose exploitation is extremely difficult, or whose impact is minimal. We recommend applying low severity updates at your discretion.
- Unspecified - The patch was issued without a severity rating.
- Critical - Vulnerabilities that can be exploited without warnings or prompts. Examples include remote elevation of privileges exploits that allow attackers to write to the file system, or execute arbitrary code without user interaction. You should patch critical vulnerabilities as soon as possible.
- Target Device Count - Number of devices affected by the vulnerability. Click this to view device details and implement patches.
- Click 'Applications' > 'Vulnerability Management'
- Click the 'Vulnerability List' tab
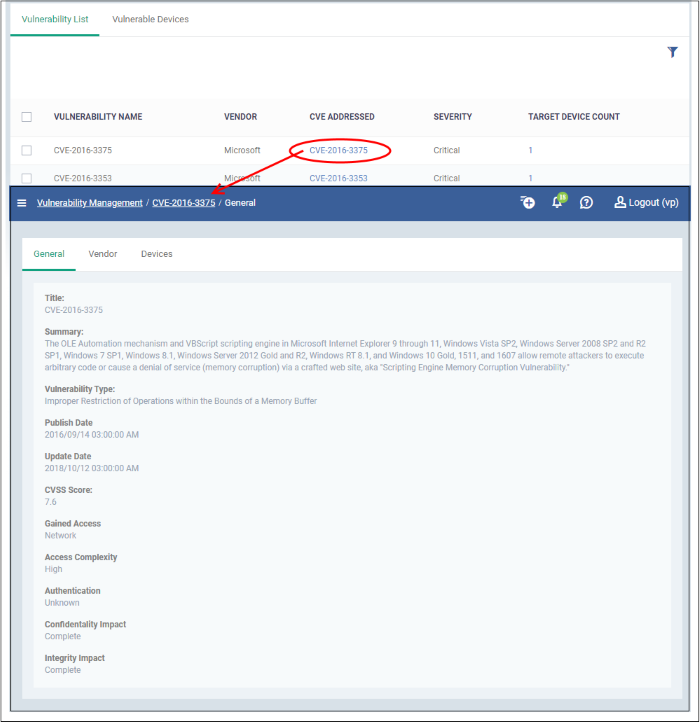
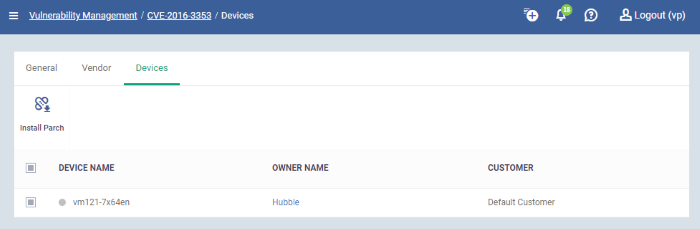
- Click the CVE ID number in the CVE Addressed column
The CVE details have three tabs, 'General', 'Vendor' and 'Devices'.
- General – Shows the details such as the vulnerability type, publication date and so on.
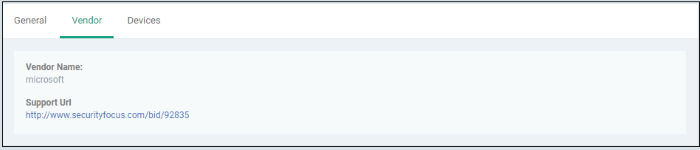
- Vendor – Shows details about the software publisher:
- Devices – Details about the devices on which the vulnerability was found:
- You can run security patches for devices from here. See 'Patch selected vulnerabilities' for more help with this.
Patch selected vulnerabilities
You can run security patches to address a particular threat.
- Click 'Applications' > 'Vulnerability Management'
- Click the 'Vulnerability List' tab
- Click the CVE ID number in the 'CVE Addressed' column
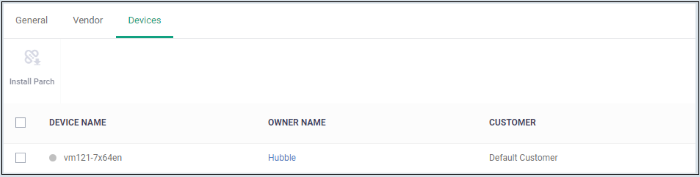
- Click the 'Devices' tab to see devices that have the vulnerability
- Select your target devices then click 'Install Patch'
Install patches on selected devices
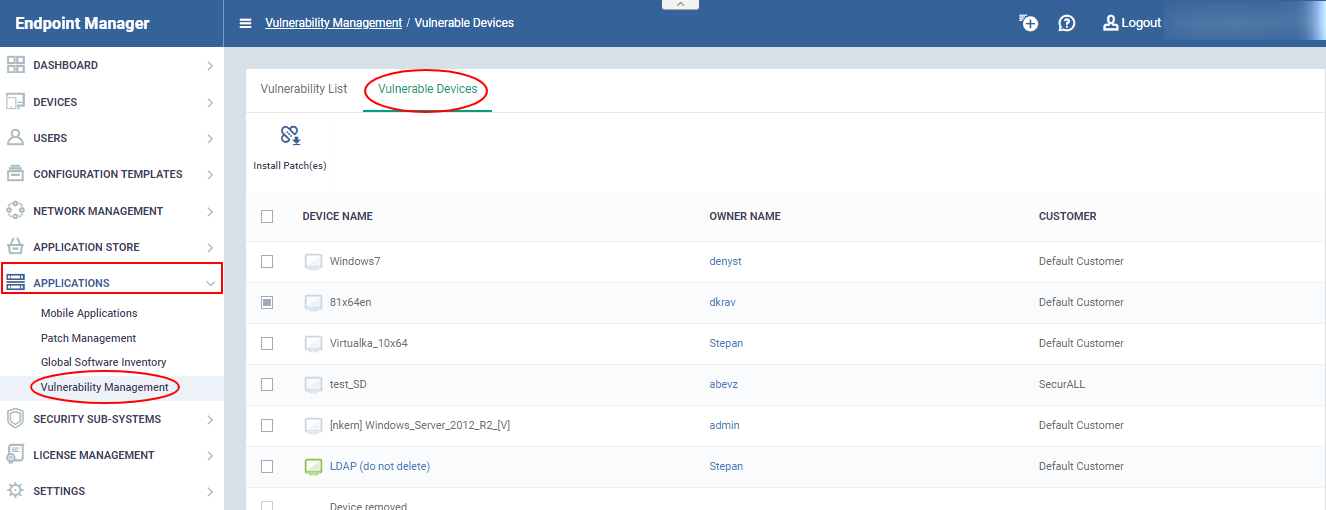
- Click 'Applications' > 'Vulnerability Management'
- Click the 'Vulnerable Devices' tab
This screen shows all devices affected by one or more vulnerabilities. You can install patches for all vulnerabilities affecting a device from this interface.The vulnerable devices list can be sorted alphabetically by all columns in the table under the Vulnerability Management
- Device Name - The label of the device that has the vulnerabilities
- Owner Name - User of the device.
- Customer - The organization to which the device is assigned.
Install patches onto vulnerable devices:
- Select the devices to apply patches
- Click 'Install Patches'